Genians ZTNA
Home Genians ZTNA
NAC - Driven Zero Trust Network Access
Accelerate Non-disruptive Zero Trust Implementation
In this perimeter-less world, where do you currently stand, as network environments continue to evolve dramatically and cyber threat surfaces continue to change and expand? Expedite securing network edges by adopting zero trust security. These two essential elements will help you solve the puzzle of how to achieve zero trust.
Digital Identity Attributes
“Never trust, always verify” – but never trust what? Define the specifics of devices accessing your network by correlating them with both their technical and business contexts in real-time.
Universal ZTNA
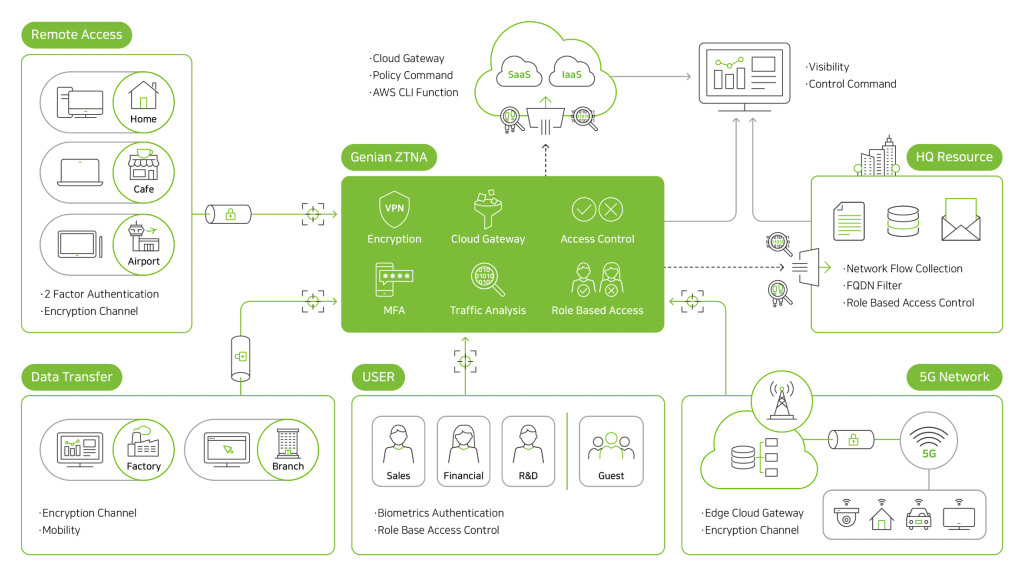
ZTNA is not only necessary for remote work. The same security and user experience should be provided anywhere—on campus networks, in branch offices, and in the cloud.
Key Features
ZTNA Anywhere Powered by Genians #1 Proven NAC
- Infrastructure Independent Network Sensor
- Device Platform Intelligence
- IP Address Management
- Switch Port Management (SNMP)
- WLAN Visibility/Security
- Traffic Flow/Analysis (Netflow)
- Micro Segmentation
- Context-based Least Privilege Access
- Multi-layered Enforcement – ARP / DHCP / 802.1x (RADIUS) / Cloud Gateway / Agent / SPAN(Mirror)
- Application Visibility and Control
- IP Mobility (VxLAN, Always on ZTNA)
- Cloud Workload Visibility
- Cloud Security Group Management Automation
- Zero Trust Security Policy for Cloud Workload
- Security Service Edge (SSE) on the Cloud (AWS, Azure, GCP)
- White-labeled SASE solution for MSSP
Secure Remote Access
- ZTNA Agent for Secure Remote Connection
- Biometric (FIDO) Authentication
- Dynamic Policy Enforcement (RADIUS CoA)
- Always on ZTNA
- IPSec / SSL-VPN Gateway
Endpoint Security
- Endpoint Visibility
- Device Configuration
- Application Management
- Compliance and Risk Posture Measurement
- Automated Remediation
Components
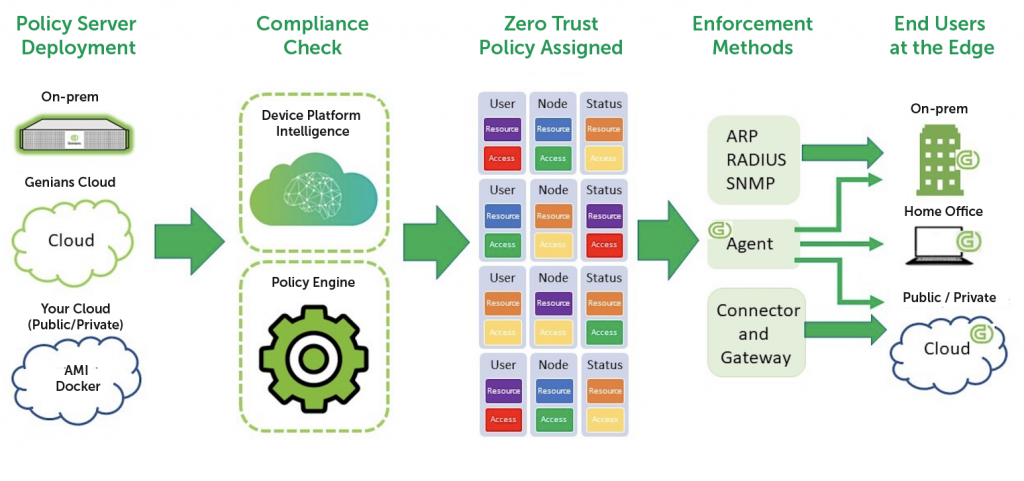
Essential elements for Genian ZTNA
Genians Cloud
- Review and refine device platform information via the cloud
- Deliver the most accurate, up-to-date device platform intelligence to Policy Server on a weekly basis.
- NAC software distribution (updated bi-monthly)
- Docs
Policy Server
- Available in Genians Cloud, Public Cloud, Private Cloud or On-Prem
- Provides single pane of glass for all ZTNA policies
- Correlates data from Sensors, Agents, and Network Devices
- Manage components, users, devices, dashboards, and reporting
- Integration options for Security Automation with Cybersecurity Ecosystem
Network Sensor
- Can be deployed on physical Intel products as VMs, Docker containers, or Agents
- Use for Public Cloud, Private Cloud, On-Prem, Branch or even Home applications.
- Provides Genian Device Platform Intelligence (GDPI) for any IP-enabled device
- Collects Network Traffic for Analysis
- Performs Policy Enforcement Functions
- Performs VxLAN Tunneling to support IP Mobility
Integrated NAC/ZTNA Agent
- Provides full NAC Endpoint Security
- Over 50 available plugins to monitor and control endpoints
- Built-in client VPN functionality
- Sensor plugin available for quick visibility at small locations
- Access Control capability utilizing dynamic firewall rules on endpoint
Cloud Gateway
- Available in Public Cloud, Private Cloud, or On-Prem
- May also be deployed as a Remote/Teleworker Gateway
- Provides Authentication Services and Zero Trust Access Control
- Controls traffic to Internet, Cloud, and On-Prem Destinations
- Application visibility and Control
Cloud Connector
- Provides Granular Control in AWS Cloud Environments
- Detects any Computing Instances Deployed
- Automated Security Group Updates
