Kron™ Database Access Manager (DAM)
Unlocking Database Security: Explore Kron™ PAM’s Database Access Manager Capabilities
The Kron™ PAM Database Access Manager provides session logging functionality to database admins. All database queries can be logged for security and compliance purposes. The user experience is unchanged as they continue to use their own database client. The client can communicate with the Database Access Manager through the standard protocol used by the database.
Kron PAM comprehensively logs all privileged session database connections and activities that may generate data breaches and impact business continuity.
Kron PAM efficiently and centrally secures and controls privileged access to databases and provides users a dedicated access to the information that is assigned to them, not any other information.

Database admins can control logging as well as user permissions to execute SQL commands, by employing policy enforcement and database masking as preventive actions.
Elevating Data Security: Dynamic Data Masking with Kron™ PAM
Data masking technology is a crucial defense against the misuse of sensitive information. It works by providing users with fictitious or concealed data, rather than exposing real and sensitive information. This proactive approach is essential for safeguarding data at rest, found in non-production databases, as well as data in transition, often encountered in production databases.
Why Dynamic Data Masking (DDM)?
Dynamic Data Masking becomes indispensable, especially in scenarios like application testing, where representative and coherent data are required. DDM is a key strategy to limit sensitive data exposure, masking it for non-privileged users. Kron PAM’s Database Access Manager employs DDM with a range of masking rules, including redaction/nulling, shuffling, blurring, tokenization, substitution, and custom rules defined by regular expressions.
Fine-Tuned Masking Control:
- Time-based Restrictions
- Geo-location Restrictions
- Maintenance Mode Restrictions
- Context-based Restrictions
- Blacklist and Whitelist
DDM allows configuration to conceal sensitive data in query result sets without altering the underlying database content. This strategic implementation ensures that while users see masked data, the actual data in the database remains unchanged.
Policy Enforcement Mastery:
Kron PAM’s Database Access Manager takes data security a step further by providing four robust methods for policy enforcement:
- Redaction/Nulling
- Shuffling
- Blurring
- Tokenization
Database admins gain granular control over user permissions, enabling them to define SQL query rules that align with established security requirements. Secure your data effectively with Kron PAM’s dynamic and fine-tuned Dynamic Data Masking capabilities.
Effortless Database Control with Kron’s DAM & DDM
Kron’s Database Access Manager (DAM) and Dynamic Data Masking (DDM) work seamlessly to fortify your database security. Acting as a man-in-the-middle proxy, DAM takes command of diverse databases—Cassandra, Hive, IBM DB2, Microsoft SQL Server, MySQL, Oracle, Teradata, and more—from a centralized hub.
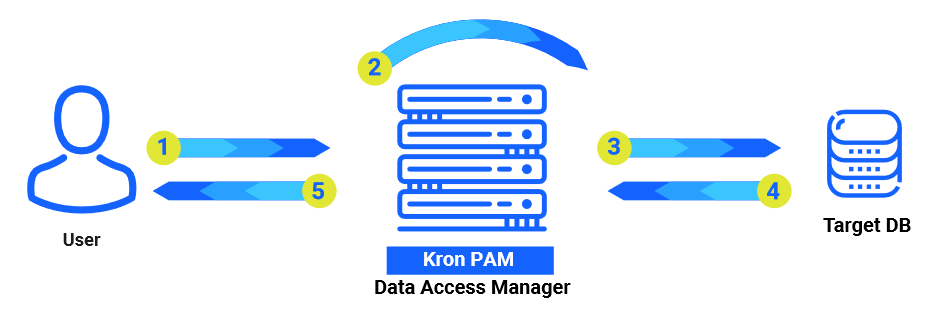
How It Works:
- User Queries Through SQL Proxy:
- User queries are transmitted to the database through the SQL Proxy.
- Policy Application by SQL Proxy:
- SQL Proxy captures user queries and applies policies.
- The synergy of Data Access Management and Dynamic Data Masking guarantees robust data security at the core, fortifying database security comprehensively.
- Real-time Monitoring:
- The proxy vigilantly monitors database activities, allowing necessary actions to proceed.
- Database Access Manager segregates records and displays query results as per authorized users while logging all data access sessions.
- Dynamic Data Masking in Action:
- DDM selectively masks individual data elements within the filtered dataset.
- The DDM engine precisely controls access rights, determining who can access what, where, when, why, and how—even down to individual cells in database queries.
Process Flow:
- User Query Execution:
- The user initiates a query.
- Logging and Rewriting:
- The query is logged and rewritten based on policy rules.
- If DDM is activated, the query passes to the DDM module for enhanced masking rules.
- The masked query is then returned to the Database Access Manager.
- Query Transmission:
- The manipulated query is forwarded to the target database.
- Result Retrieval:
- The target database returns the query result to Kron PAM’s Database Access Manager.
- Filtered Result Delivery:
- Kron PAM’s Data Access Manager forwards the filtered results securely to the user.
Experience unparalleled control and security at every step of your database interactions with Kron’s DAM and DDM integration.
FEATURES & BENEFITS
- Unified Access Control:
- Manages access control seamlessly across the database layer.
- Indisputable Query Logging:
- Logs all queries indisputably, ensuring accountability.
- Users authenticate with their own credentials, even if no specific DB user exists.
- Sensitive Data Discovery:
- Detects sensitive data like credit card or personal ID numbers in Database and Big Data servers.
- Dynamic Data Manipulation:
- Manipulates and delivers sensitive data in a way that retains coherence and usability while rendering it non-sensitive.
- Effortless Policy Assignment:
- Easily and instantly assigns policies (DB masking rules) to users, application accounts, groups, and roles.
- Progressive Data Protection:
- Minimizes the risk of data disclosure during processing.
- Time-Limited Access:
- Allows time-limited access control (hours of the day, day of the week, etc.).
- Performance-Optimized:
- Operates without performance degradation on target databases.
- Tool Flexibility for Users:
- Users are not restricted to proprietary database clients and can continue using familiar tools (e.g., Toad) without interference.
- Password Security Enhancement:
- Eliminates weak and non-expiry passwords.
- Automatically disables inactive accounts.
