Sparrow DAST
Home Sparrow DAST
Automated detection of security vulnerabilities
Automatically crawls subdirectories information from a web application’s URL & detects security vulnerabilities from crawled URLs


Comprehensive coverage
Improve the security and quality of software by complying with global security compliances guides and standard guides
OWASP Top 10 2017, 2021, CWE, etc
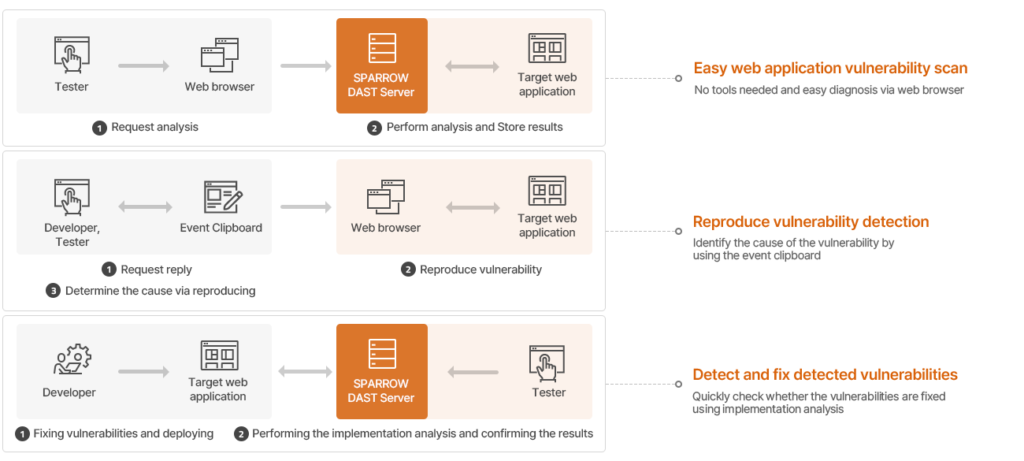
Attack process simulation
By reproducing the vulnerability attack process by events, users can quickly identify and understand the web hacking process.

Key Features
Thoroughly analyze security vulnerabilities that exist in web applications
Prevent hacking by securing the safety of the website
Web-based user interface
- Web-based user interface eliminates the need for installation and easy access via a web browser
- Centralized management of analysis results and sharing
Powerful analysis
- Detect security vulnerabilities in web applications using browser event replay technology
- Open-source web library vulnerability analysis
Interaction support
- Overcome limitation of dynamic analysis via interaction with Sparrow SAST and RASP
- IAST capability via TrueScan function
Analysis reports
- Easy to read report with clear vulnerability information and trends
- Detailed reports with analysis methods, results, and solutions for each vulnerability
Analyze the latest web
application technology
- Web application analysis using the latest technologies such as HTML5, AJAX, etc
- Vulnerability detection by reproducing various events that can be performed in the browser
Multi-user optimized system
- Set permissions and roles per user
- Centralized management of analysis results and sharing among users
Use Case
Continuous protection of web applications from external attacks